Cybersecurity, a global concern, is evident in major incidents at MGM and Clorox, causing significant revenue loss (Siddiqui, 2023; Sandhu-Longoria, 2023). Despite this, it’s often seen as optional rather than essential, overlooked by executives (Violino, 2023). In 2022, 83% of companies faced multiple data breaches (Verizon Business, 2023). In US healthcare, cases surged from 314 in 2014 to 707 recently (Petrosyan, 2023).

Leadership and Cybersecurity
The responsibility of protecting a company’s data is influenced by the “right choices” and the reasons behind those choices made by the company and its staff (Carter, 2022). Unfortunately, leaders who perceive cybersecurity breaches as catastrophic often neglect their managerial responsibility in protecting their organization from cybersecurity threats (Schultz, 2005). This perspective emphasizes that cybersecurity is not solely a technological concern but also a sociotechnical issue, recognizing that an organization’s weakest link is often its human element (Triplett, 2022).
In fact, 88% of companies acknowledge that cybersecurity is a known risk within their organization, and 64% of them are considering a shift in their economic model from profit-focused to technology-focused (Gartner, n.d.). The lack of corporate accountability and leadership highlights the need for more proactive measures to capture the attention of Chief Executive Officers and Board of Directors (Hathaway, 2012). Notably, it wasn’t until regulations were enacted in 2011 that the Securities and Exchange Commission (SEC) mandated the reporting of cybersecurity incidents, leading to increased attention from corporate leaders (Hathaway, 2012).
Moreover, it is evident that cybersecurity is often an afterthought, frequently omitted from discussions related to business models, digital strategies, decisions, and even mergers and acquisitions (Doan, 2019). While regulations and policies are implemented for large companies, questions arise regarding smaller companies with substantial databases and extensive technological infrastructure that are not publicly listed. Do these companies have the flexibility to overlook such incidents and neglect their focus on cybersecurity? This raises important concerns about the cybersecurity practices of non-publicly listed organizations.

Ethical Responsibility of Cybersecurity Leaders
Ethics serves as the standard for determining what is right or wrong and guides the actions individuals take in specific circumstances (Sennovate, 2023). Unlike professionals such as doctors and lawyers, who have common codes of conduct governed by law, cybersecurity professionals are guided only by a code of conduct based on responsibility and ethics; which are teleological ethical principles (Sennovate, 2023). The duties of a cybersecurity professional mainly include creating frameworks, processes, and procedures for organizations, as well as identifying security vulnerabilities in their infrastructure and largely based on their teleological principals of ethics (Augusta University, n.d.). However, the lack of a clear regulatory framework means that these professionals operate primarily on teleological ethical principles.
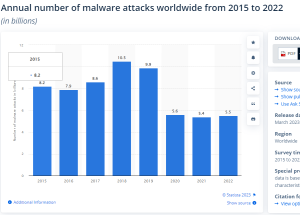
When cybersecurity leaders or professionals carelessly, fraudulently hide, or disclose vulnerabilities within an organization, or when such professionals are not taken seriously, the impact on the organization can include reputational and monetary damage (RiskOptics, 2021). The increasing attention to cybersecurity from the public is evident, as seen in the reduction of malware attacks from 8.2 billion in 2015 to 5.5 billion in 2022 (Petrosyan, Annual number of malware attacks worldwide from 2015 to 2022 (in billions), 2023).
Ethical hacking, also known as “white hat” hacking, is one area where teleological principals of ethics are prominent in the cybersecurity industry. Ethical hackers are security experts who assess environments and attempt to breach customer locations with their arsenal of tools, reporting their findings back to the customer (Synopsys Inc, 2023). In contrast, “black hat” hackers perform similar actions without reporting and often with malicious intent (AO Kaspersky Lab, 2023). When viewed from a macro perspective, the “thin line” concerning ethics plays a crucial role in the decisions made by cybersecurity leaders.
However, there is a puzzling aspect when considering the factors that might cause a hacker to transition from “white” to “black” or vice versa. The decision-making process could involve various factors, including financial incentives. Despite these complexities, the lack of a standard benchmark for evaluating “leadership” or “ethical behaviour” in every professional interview raises questions. This gap in evaluation criteria could be due to oversight or intentional neglect, leading to uncertainty in the hiring process within the cybersecurity industry.
Conclusion
Organizations hesitate to adopt cybersecurity measures due to unclear benchmarks and high implementation costs (Gadient, 2023). A potential solution is integrating cybersecurity resilience into the ethical framework, emphasizing its importance alongside core values (IBM, 2023). Unclear definitions and responsibilities compound the challenge, underscoring the need for clarity in fortifying cybersecurity.
References
AO Kaspersky Lab. (2023). What is Black-Hat Hacker? Retrieved from Kaspersky: https://www.kaspersky.com/resource-center/threats/black-hat-hacker
Augusta University. (n.d.). Cybersecurity Ethics: What Cyber Professionals Need to Know. Retrieved from Augusta University: https://www.augusta.edu/online/blog/cybersecurity-ethics
Carter, C. (2022, 05 23). The CISO as an Ethical Leader: Building Accountability Into Cybersecurity. Retrieved from Rapid7: https://www.rapid7.com/blog/post/2021/06/24/the-ciso-as-an-ethical-leader-building-accountability-into-cybersecurity/
Doan, M. (2019, 11 27). Companies Need to Rethink What Cybersecurity Leadership Is. Retrieved from Harvard Business Review: https://hbr.org/2019/11/companies-need-to-rethink-what-cybersecurity-leadership-is
Gadient, A. (2023, 05 08). The Hidden Costs Of Cybersecurity. Retrieved from Forbes : https://www.forbes.com/sites/forbestechcouncil/2023/05/08/the-hidden-costs-of-cybersecurity/?sh=20225d4a23e3
Gartner. (n.d.). Become a Better Cybersecurity Leader. Retrieved from Gartner: https://www.gartner.com/en/cybersecurity/insights/cybersecurity-leadership
Hathaway, M. E. (2012). Leadership and Responsibility. Georgetown Journal of International Affairs , 74.
IBM. (2023). What is cyber resilience? Retrieved from IBM: https://www.ibm.com/topics/cyber-resilience
Petrosyan, A. (2023, 06 23). Annual number of malware attacks worldwide from 2015 to 2022(in billions). Retrieved from Statista: https://www.statista.com/statistics/873097/malware-attacks-per-year-worldwide/
Petrosyan, A. (2023, 08 03). Healthcare data breach U.S 2022. Retrieved from Statista: https://www.statista.com/statistics/1274594/us-healthcare-data-breaches/
RiskOptics. (2021, 02 26). The Importance of Ethics in Information Security. Retrieved from RiskOptics: https://reciprocity.com/the-importance-of-ethics-in-information-security/
Sandhu-Longoria, A. K. (2023, 10 05). Clorox ransomware attack which caused product shortages linked to earnings loss. Retrieved from USA Today: https://www.usatoday.com/story/money/2023/10/05/clorox-cyberattack-earnings-loss/71072256007/
Schultz, E. (2005). The human factor in security. USA: Comput. Sec.
Sennovate. (2023, 02 02). The Ethics of Cyber Security: Sennovate. Retrieved from Sennovate: https://sennovate.com/the-ethics-of-cybersecurity-debating-the-gray-areas/
Siddiqui, Z. (2023, 10 06). Casino giant MGM expects $100 million hit from hack that led to data breach. Retrieved from Reuters: https://www.reuters.com/business/mgm-expects-cybersecurity-issue-negatively-impact-third-quarter-earnings-2023-10-05/
Synopsys inc . (2023). Ethical Hacking. Retrieved from Synopsys: https://www.synopsys.com/glossary/what-is-ethical-hacking.html#B
Triplett, W. K. (2022). Addressing Human Factors in Cybersecurity Leadership. USA: J. Cybersecur. Priv.
Verison Business. (2023). 2023 Data Breach Investigations Report. Retrieved from Verizon Business: https://www.verizon.com/business/resources/reports/dbir/
Violino, B. (2023, 07 24). A critical cybersecurity backup plan that too many companies are ignoring. Retrieved from CNBC: https://www.cnbc.com/2023/07/24/the-critical-cybersecurity-backup-plan-too-many-companies-are-ignoring.html




Very Interesting writeup. got to agree on those points mentioned.
Sadly sometimes it ends up being cheaper to deal with the repercussions of the attack than to maintain a level of cybersecurity.
Agree, a lot of them would literally just wind down instead of fixing them
The pressing issue of cybersecurity is often overlooked by company leaders despite the significant financial and reputational risks. The lack of clear benchmarks and regulatory frameworks for evaluating ethical behavior in the cybersecurity field raises important questions about how to ensure accountability and protect organisations from evolving threats. It underscores the necessity for integrating cybersecurity resilience into the ethical framework to emphasize its importance and provide clarity in fortifying cybersecurity.
“What an insightful blog on the critical intersection of compliance and ethics in cybersecurity! It’s a complex challenge that leaders in this field face daily, and your article provides a thought-provoking exploration of the dilemmas they confront.
Great article on the discussion on dangerous choice between compliance and ethics leaders took on cybersecurity. Very informative with Ethical Responsibility with the compliances with Cybersecurity Leaders.
Very insightful article highlighting the importance of ethical hacking. It clearly distinguished the white hat and black hat theory in the cybersecurity space.
There is no clear definition between the white and the black … I can see some white hat hackers extorting the customers in my line of work …
The article brings to the forefront the vital ethical role that cybersecurity leaders play. Unlike other professionals who adhere to well-defined legal codes, those in the cybersecurity field operate based on their ethical principles. The exploration of ethical hacking, with a clear distinction between white hat and black hat practices, adds a layer of complexity and intrigue to the discussion.
In summary, no clear line can be drawn…. as yet…!
As someone who works in the cybersecurity industry I enjoyed the read and I agree with your points. I think the points around “recognizing that an organization’s weakest link is often its human element” makes it so true as to what reality is and it identifies what we should and should not do to work around it.
Not a joke the amount of effort someone needs to bring to just get management approval on “cyber security” situation .
The blog is very well structured and very informative in less amount of words. The pictures which are used are very catchy.
Great article to read. Yes agree that Organizations hesitate to adopt cybersecurity measures due to unclear benchmarks and high implementation costs. I think it is because some organisation do not understand the risk until they face a real damage.
Reading this blog triggered my curiosity on Cyber Security Standard. To my basic understanding there is a standard for Cyber Security and that is ISO/IEC 27032. So companies are not compliant on this standard? or the Standard is not enough? Isn’t there any audit on Cyber Security?
Self audit is the basis on cybersecurity until shit hits the fan